
Per Vestige Digital Investigations, there are options when considering how best to approach certification to CMMC. (Photo credit: U.S. DOD)
While some would argue that an organization’s compliance with U.S. Department of Defense (DOD) cybersecurity regulations (NIST 800-171) and the newly minted Cybersecurity Maturity Model Certification (CMMC) are arduous requirements, that’s not an accurate perspective. For cybersecurity practitioners, we tend to feel these frameworks are the bare essentials, representing best practices that all organizations should be following to protect their own sensitive information, let alone Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). Regardless, you’ve likely rightfully concluded that you need to comply (forced or unforced) and, as such, are now looking to determine how to get there.
The primary reason is: Our adversaries want our information.
It’s no secret that our adversaries are always interested in gaining any upper hand they can. If that means stealing intellectual property or gaining access to sensitive defense information — even by way of breaking into our computer systems — so be it. If all our nation’s sensitive information was stored in one central system and we put all of our resources into securing that information, we might be in a better place than we are. However, that’s not how it works.
Intellectual property and our sensitive information is often found in the hands of prime contractors and subcontractors strewn around a delicate balance of computer systems — most of which are not adequately secured for the organizations’ own sensitive information, let alone the information entrusted to it by the U.S. government.
The DOD’s initial attempt at bringing this under control, NIST 800-171, has awkwardly been met with resistance or downright lack of awareness that organizations need to follow it. And, while there are penalties for noncompliance, they are back-end loaded with the damage having already been done by the time it is determined that an adversary has gained access and exfiltrated sensitive information.

Olson Custom Designs is a shop specializing in defense-industry contracts. Today, more than 80% of the shop’s work is for DOD projects. Although the company’s own data security has never been compromised (at least not to anyone’s knowledge), it has heeded the lessons of incidents experienced first-hand by team members at their past employers. Learn more about it’s CMMC efforts at gbm.media/olson-923. (Photo credit: Olson Custom Designs)
CMMC functions differently. Gone are the days of self-assessing your compliance with NIST 800-171 because it requires an outside CMMC Third Party Assessing Organization (C3PAO) to agree you have the appropriate controls in place. Also gone are the days of back-end loading the requirements because a CMMC-designated contract requires, for the most part, entities working on the contract to be certified at or above the maturity level required by the contract prior to being awarded the contract. As a result, it’s righting the equation and putting the horse back in front of the cart.
Our adversaries want our information.
There are a number of other nuances that need to be taken into consideration, including understanding the difference between FCI and CUI, what the various maturity levels mean and the addition of processes into the mix, including much more poignant policies, procedures, plans and so on.
Suffice to say, the bar has been raised. And, while this is a good thing overall for the security of the United States’ sensitive information, many organizations are woefully unprepared for this change. What’s worse is there’s much misunderstanding about what it takes to become compliant — misunderstanding about the timing, the requirements and, most notably, how to implement the practices and processes in such a way as to pass the assessment and obtain certification.
Like most things in life that are perceived to be difficult, everyone is looking for the silver bullet, that magic solution which can be implemented with minimal effort. Unfortunately, there is no easy button with regard to CMMC. Sure, there are all kinds of solution providers that can make it easier, but there will be no simple wave of the magic wand and you’re now compliant. This means organizations must evaluate their options.
CMMC Choices
So, what are your options and which makes most sense for your organization? It’s first important to understand that only about 50% of the requirements of CMMC are true “technology” requirements. Roughly 25% of the requirements are “administrative” (think policies) and the rest are “operational.” When you understand that, you can start to understand why no silver bullet can address it all.
In short, here are your most viable options:
- Do it yourself
- Work with an outside IT company
- Hire a cybersecurity company
- Engage a Registered Practitioner Organization (RPO) which is part of the CMMC ecosystem
- Bring in a C3PAO (also part of the CMMC ecosystem) in a consultative approach
- Engage with a CMMC solution practitioner that specializes in cybersecurity, compliance and CMMC (RPO or C3PAO).
The DIY Approach
The good news about CMMC is there is no requirement specifying that you use professionals to prepare your organization for the certification. Many organizations will, in fact, choose this route. The advantages, of course, are that cash outlay for outside services is minimized if not eliminated altogether. If you are considering going it alone and using internal IT staff, internal compliance individuals or others to prepare for compliance, you’ll want to ensure that you set yourself up for the best success. CMMC compliance, in general, is a tricky thing as you need to make sure in reviewing the framework’s control objectives that you thoroughly understand what those requirements really mean. Far too often, I have seen organizations “believe” they know what the requirement is, proceed to implement their perceived solution, only to find out that they had woefully misunderstood the requirement. I’ve actually seen this go both ways: believing what they’re putting in place is enough to comply with the requirement and putting in place procedures that far exceed the requirement.

Leadership at Olson Custom Designs says the work associated with CMMC is similar to what the company has done to achieve quality control certifications such as AS9100 and ISO. Like these requirements (and unlike previous cybersecurity standards), CMMC will require third-party certification. (Photo credit: Olson Custom Designs)
Even more important, however, is ensuring those who are involved have experience with an evidence-based assessments. The job of an outside assessor, such as the C3PAO, is to evaluate your organization in enough detail to form an opinion as to whether you have the required controls in place and they are working as designed. This can be a tall order, considering that the C3PAO needs to collect enough evidence to put into their work papers when they turn the assessment results over to the CMMC Accreditation Body (CMMC-AB). From there, the quality assurance assessors of the CMMC-AB review the C3PAO’s work papers (including evidence) to come to the same conclusion as the C3PAO as to whether the organization has achieved the requirements.
And what is that evidence? The CMMC-AB has provided guidance to the C3PAOs that for each control objective, the C3PAO needs to collect and document a minimum of two pieces of corroborating evidence with no more than one piece of evidence coming from each of interviewing subject matter experts, direct observation of a practice/process being carried out or testing.
The Outside IT Approach
Choosing to work with your outside IT company can offer many benefits as well. After all, they know your environment. They’re probably extremely knowledgeable about the practices and processes in place and, in fact, are likely part of the process. If you subscribe to a Managed Service Provider’s (MSP) service, it is quite likely they have put into place a lot of the best practices that are encapsulated in the CMMC framework. This can save time and effort, which translates to less cost. The big consideration here is ensuring they understand the cybersecurity requirements, interpret the framework’s control objectives correctly and understand the nuances of the CMMC framework. There’s also the subtle, but pesky little issue of whether there’s a perceived conflict of interest — after all, if you expect them to have already put the best practices in place, will their assessment accurately reflect the true status of your environment if their own performance would be called into question?
The Cybersecurity Professional Approach
CMMC is about information security and cybersecurity is a type of information security, so what about hiring a cybersecurity professional? This can be a good option, but, just like any profession, specialization is key.
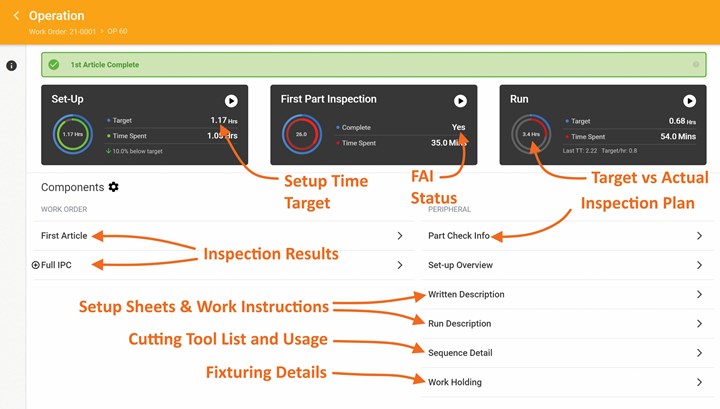
According to Olson Custom Designs, ProShop ERP helps make the machining business scalable by facilitating a largely paperless workflow, which customers and prospective customers tend to notice. From the moment a request for quote (RFQ) is entered into the ERP system, all digital documentation associated with a job remains associated with that job, from purchase orders and material certifications to quality documents and data associated with providers of heat-treat, plating and other outside services. Proshop ERP offers CMMC-specific tools, including “work orders” that guide staff through checking off requirements in the same way that shop-floor work orders guide them through machining parts. (This annotated Proshop ERP screenshot of a work order depicts the use of hyperlinks to connect all data associated with a job.) Olson Custom Designs says working with the various templates, checklists, explanations of requirements and other resources embedded in the software is similar to its earlier efforts to attain ISO and AS9100 certification. (Photo credit: ProShop ERP)
There are many facets to cybersecurity, including implementation of software or hardware solutions, monitoring, architecting a secure system and even compliance. The first task in evaluating a cybersecurity professional firm is ensuring it focuses on compliance. After all, CMMC is all about complying with the cybersecurity framework.
Additionally, you must ensure it is familiar with the nuances of the CMMC framework. While the CMMC framework is “nonprescriptive” (meaning it tells you what you need to do, but not how to do it), there is vast room for interpretation, at least until it comes time for the C3PAO to evaluate the environment. Ensure that any cybersecurity professional firm you evaluate has intimate knowledge of the framework. Familiarity with Federal Acquisition Regulation (FAR) and Defense Federal Acquisition Regulation Supplement (DFARS) rules will help ensure they understand the seriousness and sensitivity of the requirements.
The RPO Approach
The CMMC ecosystem includes a number of roles and entity types that might prove to be very useful in your CMMC journey. RPOs are required to employ or align with registered practitioners (RP) that have undergone specific training related to the CMMC framework and have had to pass a competency test. This helps ensure they have the baseline knowledge to appropriately advise organizations seeking certification as to what the control objectives of the framework mean and how the certification process works while demonstrating a level of commitment to the CMMC process that other previously mentioned options don’t address.
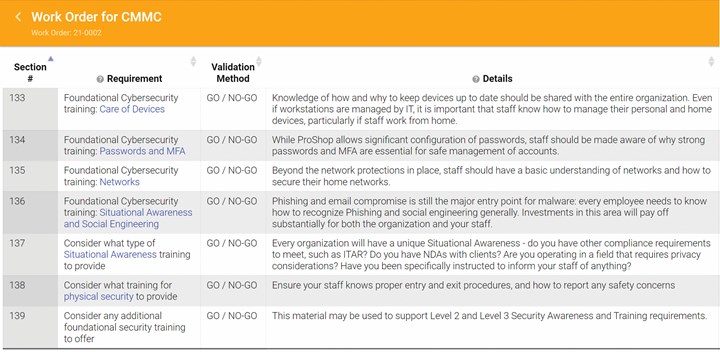
Proshop ERP offers CMMC-specific functionality to help guide machine shops through compliance. Although ERP is a critical tool, Proshop ERP emphasizes that its system’s CMMC functionality is not meant to handhold, but rather to provide a template for shops to develop individualized cybersecurity policies. (Photo credit: ProShop ERP)
Finally, RPOs are bound to a code of conduct consistent with the CMMC accreditation body’s viewpoint. There are many positives in choosing this route, but consider what experience they have with regard to remediation. While many RPOs can do a great job assessing an organization and telling you whether you are in or out of compliance, they might not be able to offer guidance as to how to get you over the CMMC finish line.
The C3PAO as a Consultant Approach
Another good choice is hiring a C3PAO in a consultative role. While ethics and requirements of the CMMC prohibit a C3PAO from being both a consultant and the certifying assessor for the same entity, there are no restrictions on a C3PAO assisting nonconflicting clients with their CMMC preparedness. As part of the CMMC ecosystem and the ones responsible for determining an organization’s fitness in achieving CMMC, C3PAOs, like RPOs, can be a great choice. They understand the nuances of the framework which can be a huge help in getting your organization ready. But, again, make sure they have deep experience with the remediation and being able to answer the “how to get there” question.
The Professional Solution Practitioner Approach
Lastly, you could engage with a professional solution practitioner that offers cybersecurity, compliance and CMMC expertise. These are cybersecurity professionals who specifically focus on compliance and understand the intricacies of compliance frameworks such as CMMC. Many have conducted hundreds of engagements assessing, advising and preparing their clients to meet compliance with a variety of frameworks. This gives them a perspective on what works in a wide range of organizations and the specific situations an organization finds itself. This, coupled with being an RPO or C3PAO, offers a valuable solution in which it has demonstrated its commitment to the CMMC ecosystem, will understand the nuances of the requirements and has the requisite experience, know-how and expertise to implement. The perceived “downfall” can be the cost, although this can be justified after considering the speed and efficiency with which CMMC can be achieved.
Start Your CMMC Journey Soon
Achieving CMMC is likely a big deal for your organization. Otherwise, why take on the effort to do so? With that much at stake, it’s important to carefully plan your CMMC journey. What you don’t want to do is engage the C3PAO for your certification assessment only to find that you are not adequately prepared. Because CMMC is an all-or-nothing venture, your only recourse for not meeting the satisfaction of the C3PAO on one or more controls is a short, 90-day “cure period.” Otherwise, you’re relegated to having to repeat the process again, which can be a costly mistake.
And, keep in mind, preparing for CMMC in-house can easily take 12 to 18 months. With an expert, that time frame can be shortened. Choosing the right path forward as you start can have a profound impact on the success of your journey.
About the Author: Damon Hacker, MBA, CISA CSXF, CMMC-RP, is the president, CEO and founder of Vestige Digital Investigations, a leading compliance-driven cybersecurity and digital forensics solution practitioner.
Read Next
Do You Have Single Points of Failure?
Plans need to be in place before a catastrophic event occurs.
Read More5 Aspects of PMTS I Appreciate
The three-day edition of the 2025 Precision Machining Technology Show kicks off at the start of April. I’ll be there, and here are some reasons why.
Read MoreA Tooling Workshop Worth a Visit
Marubeni Citizen-Cincom’s tooling and accessory workshop offers a chance to learn more about ancillary devices that can boost machining efficiency and capability.
Read More












.png;maxWidth=300;quality=90)





